
Making Your Business "Spoof Proof"
Understanding Spoof Emails
Spoof emails are fraudulent communications that appear to come from trusted sources but are sent by malicious actors. Their primary goal is to deceive recipients into performing harmful actions, such as sharing sensitive information, clicking malicious links, or downloading malware. These emails are a common tool for phishing attacks, a broader category of cybercrime targeting individuals and businesses alike.

Mimicked Trusted Entities
Spoof emails often impersonate banks, government agencies, or well-known companies to build trust.
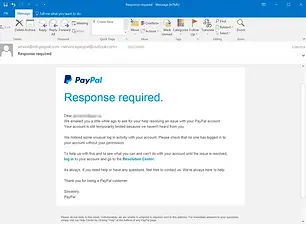
Using Realistic Graphics & Language
Many spoof emails replicate the logos, language, and design of legitimate institutions to appear credible.

Creates Urgency
They may include threats such as account suspension or fraudulent charges to prompt hasty action.

Malicious Links or Attachments
These emails frequently include links leading to fake login pages or attachments that install malware when opened.
What Are Spoof Emails?
Spoof emails use forged sender addresses and deceptive messaging to trick recipients into believing they are genuine. Attackers often manipulate the "From" field of an email to display a familiar name or domain. For example, an email may claim to be from "[email protected]" while actually originating from a fraudulent address like "[email protected]."
Who Do They Target?
Spoof emails can target:
-
Individuals/Employees: Phishers often aim to steal login credentials, financial information, or personal data.
-
Businesses: Attackers may impersonate executives in business email compromise (BEC) schemes, instructing employees to transfer funds or share sensitive company data.
-
Institutions: Universities and public organizations are common targets due to their diverse user base and extensive networks.
How to Spot Spoof Emails
-
Check the Sender Address: Look for inconsistencies in the domain name or unusual formatting.
-
Hover Over Links: Verify where a hyperlink directs before clicking.
-
Look for Generic Greetings: Legitimate organizations often address you by name.
-
Verify Urgent Requests: Contact the organization directly using official communication channels.
-
Avoid Clicking Attachments: If unsure about an attachment, confirm its legitimacy before opening.
This actually happened...
A recent example involves emails impersonating university administrators. At the University of Virginia (UVA), a phishing email urged recipients to verify their accounts within 24 hours to avoid losing them. The email employed urgency and a fake link mimicking UVA’s login page. This fraudulent URL redirected users to a malicious site designed to steal login credentials. Similar tactics were observed in phishing attempts at the University of Michigan and other institutions, which highlighted the use of mismatched email domains and spoofed sender addresses to mislead recipients.
Safeguarding Against Spoof Emails
-
Implement Email Filtering: Use advanced email security solutions to identify and block suspicious emails.
-
Educate Employees: Regular training helps staff recognize and report phishing attempts.
-
Enable Two-Factor Authentication (2FA): Adding a layer of security can prevent unauthorized access even if credentials are compromised.
-
Report Suspicious Emails: Most organizations have dedicated IT teams or resources for handling potential phishing threats.
For further insights into phishing and to view examples of such emails, visit UVAInformation Security and University of Michigan Safe Computing【10】【11】.
You Just Read A Tech News Story From The Millennium Group Computing
You might also like..

Celebrating 25 Years!
The Millennium Group Computing, a veteran-owned Managed Service Provider (MSP) based in Denver, Colorado, is proud to announce its 25th anniversary.

Free Business Analysis
Unlock the potential of your business with our 'Free Analysis' offer. Dive into a comprehensive evaluation of your technology and network security to identify opportunities for enhancement and protection.



