Phishing Emails: Questions asked & what you need to know
- amber1888
- Jun 7, 2024
- 3 min read
In This What Do I Do Series We are going to look at this:
How to Recognize a Phishing Email
Phishing emails are email scams that try and get personal or private information from individuals. This is done in an attempt to try and hack accounts or get money directly from businesses or individuals. These types of scams pull more than $3 billion per year from their victims, and need to be reported to prevent further damage and abuse.
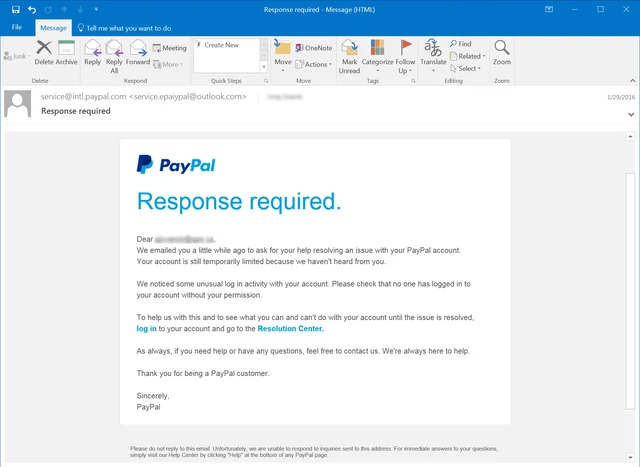
However, many of these scams have gotten complex and look very real, as they generally pose as sites or services individuals are familiar with.
You will notice a couple of things when trying to identify a phishing attack.
The email address doesn't match an email that you have ever gotten an email from.
This is the first time you're hearing of an issue with a business account that you didn't know you even had.
The language isn't consistent. Spelling errors, non-typical phonetics and sentence structure.
The email is from a brand you recognize but the email address that sent it is odd or not from their website domain. This is called "Brand Spoofing".
Brand spoofing is when a criminal pretends to be from a company or organization you trust and they use this brand recognition to trick you into giving up your sensitive information. For example, a criminal might send you an email with a logo from Google or Microsoft in the header pretending to be from them asking for your password.

What Do Phishing Emails Look Like?
These emails are designed to look like legitimate offers or statements, and are sent by email to fool the recipient into downloading a virus or providing personal information like credit card numbers or social Security numbers. Many of them are filled with urgent requests with directions to click on subsequent links– and these links can give hackers information or allow malware to be installed on your device.
It's a safe assumption to not trust any link within an email from a sender that looks abnormal.
However, there are generally some ways to identify these emails as not originating from where they state they are coming from. One common red flag to look for are language that is filled with mistakes or inconsistent grammar. Also look for inconsistencies in the sender’s email address, or inaccurate links or domain previews.
What Happens When You Click On It?
It’s unlikely for your information to get stolen or for a virus to be installed on your device simply by opening up an email. Most of the programming in these scams requires some sort of link within the email to be clicked, or for an attachment to be downloaded. However, many of these scams can be very convincing, and clicking on a link can do a lot of damage and create a multitude of headaches.
When these links are clicked or attachments are opened, most are designed to receive information about your device or other basic information that can be exploited like your contacts. This allows for them to send similar messages to the rest of your contacts. Clicking on these items can also allow malicious software to be installed without your knowledge, and this can do anything from collect confidential data to allow remote access to your computer.
What to Do When You Receive a Phishing Email
Well if you are currently working with TMGC you will already have the pre-installed email feature that alerts you of the potential phishing attempt, and you can click “report phishing” at the top of your email.
If you don’t 🙁 currently have TMGC as your Technology Service Provider depending on your email platform, there are various steps to take to report a phishing email. Most platforms have made it easy to report spam or other types of suspicious emails, and this can usually be done by selecting the email and then navigating the tool bar to find where to report it.
If you receive an business email that looks suspicious in any way, it’s better to err on the side of caution.
Utilize the Is It Phishing Tool on our website.
Reach out to your technology team and request their preferred method of reporting/investigation.
If you recognize the company but not the sender- you should compose A SEPARATE EMAIL and send them a message to a trusted email, and ask them about the suspicious message. For example, if you receive an email from your bank or credit card that seems out of place, reach out to them locally (even by walking in) to see if it’s legitimate.
It’s also important to report all suspicious email to prevent more individuals from being affected in the future especially if it came through to a work email.











Comments